
HIPAA One®
Your HIPAA Compliance Software Solution
- 7,000+ Locations
- 100% OCR Acceptance
- 3x YoY Efficiency Gains
Get a HIPAA One Demo
Trusted by 64,000+ Providers




















Simple, Affordable, Automated Solutions to Complete Your HIPAA Security Risk Assessment
Take the confusion out of HIPAA compliance with our step-by-step approach to risk analysis, remediation and documentation.
HIPAA One®, Intraprise Health’s cloud-based software, suite provides healthcare organizations with the tools to maintain compliance across operational processes.
HIPAA Compliance Software
Our HIPAA One software allows you to effectively complete your HIPAA Security Risk Assessments in a timely and painless manner.
Designed from the ground up for health care, our HIPAA compliance software follows NIST methodologies to ensure clients meet mandated HIPAA security, privacy, and breach requirements. The software guides organizations through each step of the compliance process, from assessment and development of a remediation plan to tracking the progress of implementation.
HIPAA Compliance Software Key Features
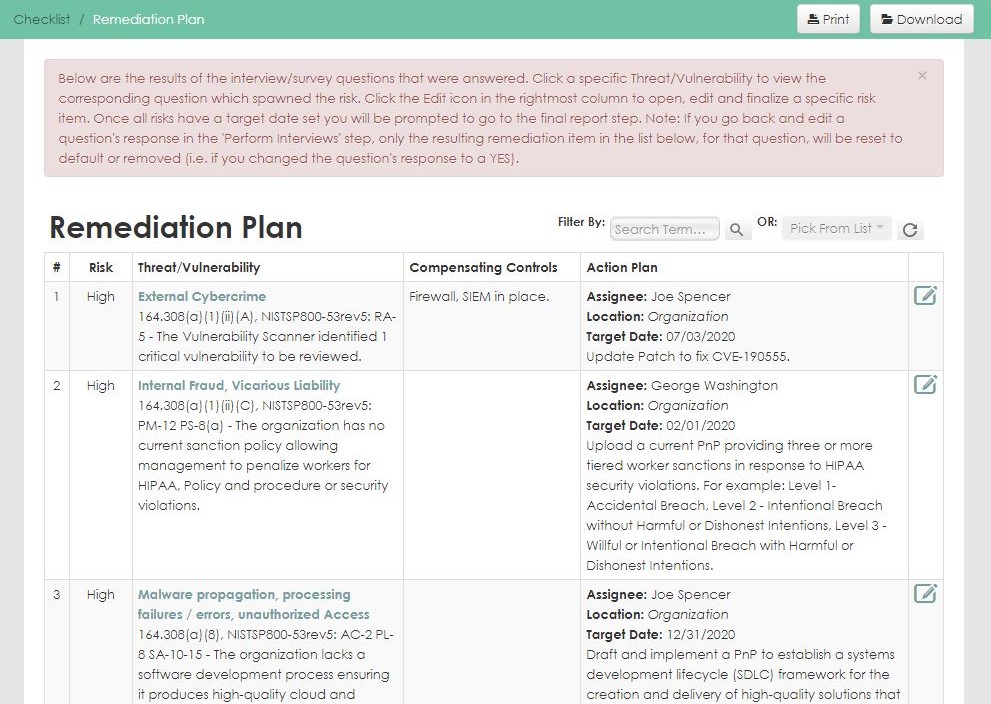
- Calculated risk assignment and prioritization
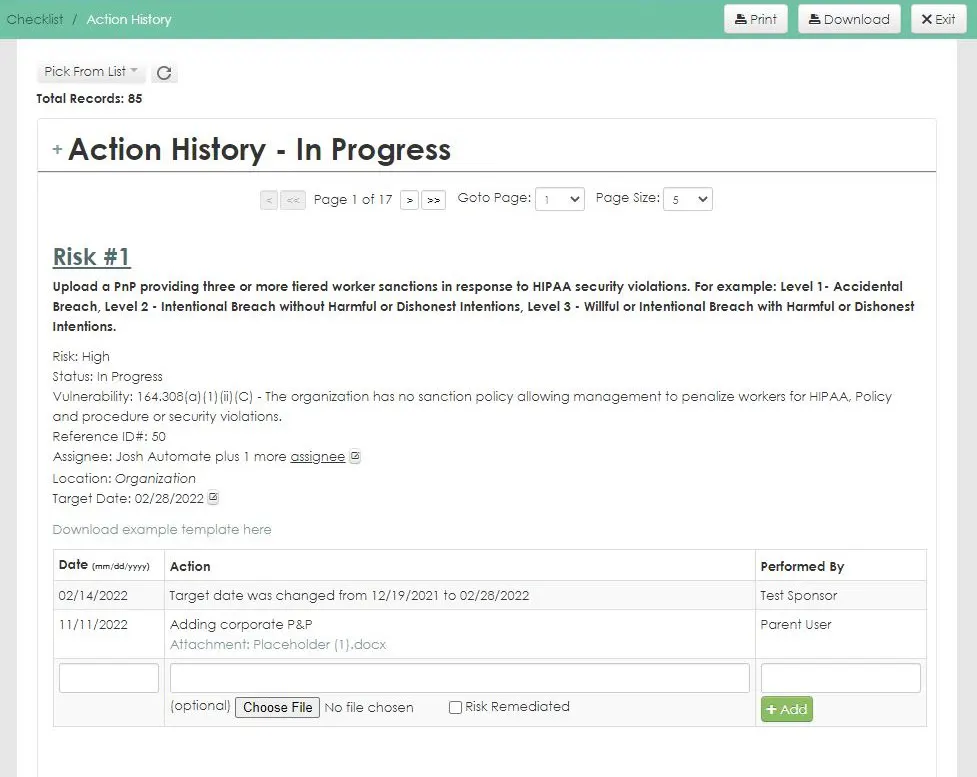
- Remediation tracking and action history
- Automated task reminders and regulation update alerts
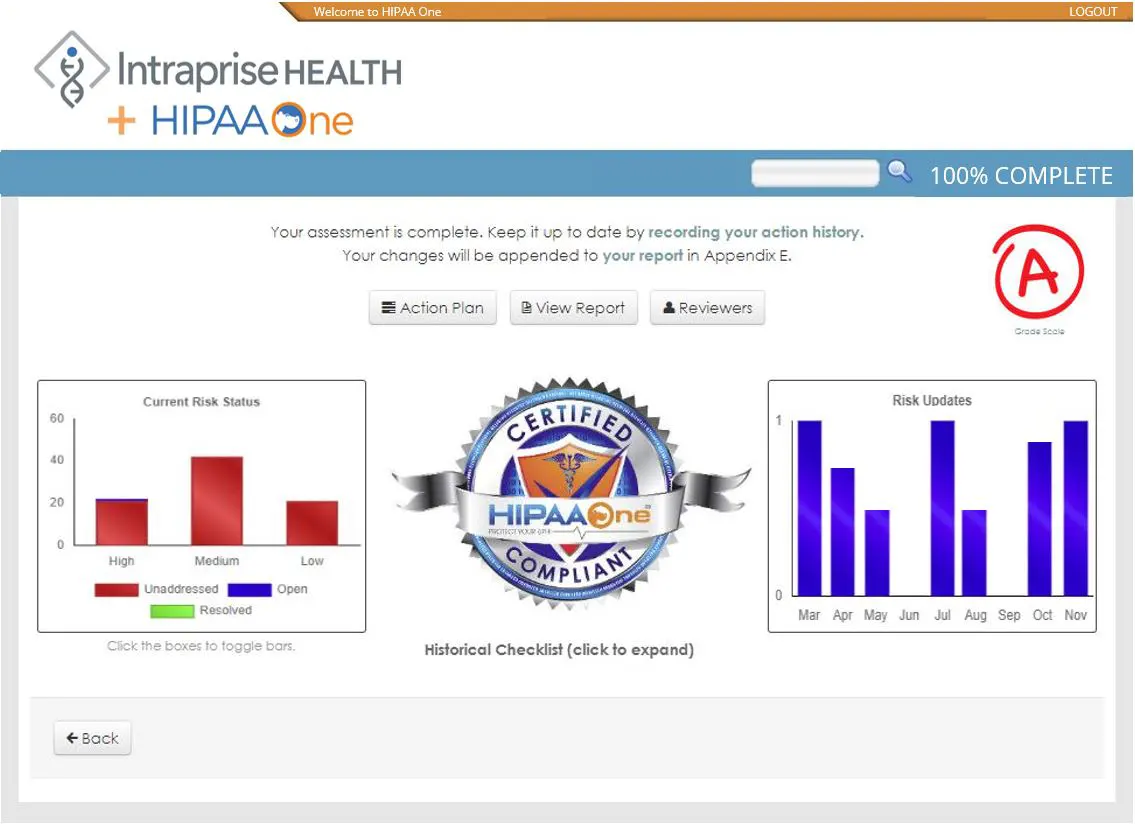
- Real-time reporting and final reporting
- Year over year import of prior assessments
- Compliance resources and checklists
The Intuitive HIPAA Compliance Solution
User-Friendly
Easily navigate complex questions and processes with a user-friendly interface, simplified citations, and useful collaboration features.
Customizable
Configure the software to meet your organization’s unique needs with customizable security settings, reporting, integrations, and more.
Supportive
Receive fast assistance for troubleshooting, technical issues, or other questions with live chat and widely available customer support.
HIPAA One® Software Suite
Security Risk Assessment
Automates the labor-intensive, error-prone activities of your annual HIPAA security risk assessment with step-by-step guidance though the assessment process.
Privacy/Breach Assessment
Easily assess vulnerabilities of privacy practices and data on all devices, applications, and networks across your organization.
Workforce Training
Online courses make effective HIPAA workforce training affordable for small practices and large organizations.
Already a user? Log in here.

Are you HIPAA Compliant?
Take this 5-minute Compliance Quiz to see where you stand
Why Healthcare Organizations Choose HIPAA One®
Get a HIPAA One Demo
Additional Resources

Blog

Cybersecurity Checklist

Case Study
HIPAA compliance software is a solution or platform designed to help organizations manage the entirety of the HIPAA compliance process, from risk assessment and analysis to remediation. Compliance software also possesses automation and centralized documentation to promote efficiency gains and ensure that nothing falls through the cracks when it comes to compliance.
When looking for HIPAA compliance software, look for a platform that has a robust array of features that can handle the entire HIPAA compliance lifecycle. Your software should also provide expert guidance throughout the process. HIPAA One is the only 100% healthcare-focused solution and provides a unique mix of automation and step-by-step guidance to help you through every step of the compliance process.
Your HIPAA compliance software should feature:
- Self-audit and guided audit options
- Remediation plans
- Workforce training
- Policies & procedures
- Business Associate management
- Incident management
- Centralized documentation
The cost of HIPAA compliance software varies based on number of providers, locations and PHI systems. The size and complexity of the environment requires different software features.
A 15-minute information gathering call will provide Intraprise Health with enough information to provide a cost estimate for HIPAA One®.
HIPAA One® software has a 100% success rate in passing compliance audits. This is because HIPAA One® follows the OCR’s Guidance Document’s requirements to protect PHI.
Competing priorities and lack of time make it challenging for healthcare organizations to stay current with state and federal legislative requirements. HIPAA One® simplifies the Security Risk Assessment process by incorporating a comprehensive library of policy and procedure templates and the tools required to maintain compliance:
- Easily add delegates, send automated reminders, and build customized reports
- System-generated risk ratings and remediation recommendations reduce underestimating potential risks
- Leverage a team of industry experts (Assessor team) to help navigate the automated process
Security resource scarcity is a top concern for healthcare executives and IT leaders. HIPAA One® automates the SRA process allowing your organization to build a culture of HIPAA compliance while saving time and money with lower resource requirements. Our 100% OCR audit pass rate provides peace of mind and patient data protection to the best of your ability.
There is no software implementation, as this is a cloud-based solution. Our customer success team, depending on the service engagement, will provide the end user with the necessary setup, provisioning, training, and measures to ensure a successful engagement using our platform. This provides ease of implementation and adoption for the clients we serve.
Intraprise Health clients achieve implementation success with HIPAA One®. Over 64,000 completed SRAs realized a 100% pass rate in OCR audits. Ninety-five percent of all assessments are started and executed in the same calendar year.
